Host Header injection to redirect in live website
The HTTP host header injection is an attack in which a malevolent actor tampers with the host header in a client request. This misleads the virtual host or intermediary system to serve poisoned content to the client in the response.
The purpose of the HTTP Host header is to help identify which back-end component the client wants to communicate with. If requests didn’t contain Host headers, or if the Host header was malformed in some way, this could lead to issues when routing incoming requests to the intended application.
let’s go to report,

Vulnerability Description:
Open redirection is sometimes used as a part of phishing attacks that confuse visitors about which web site they are visiting.
Remediation:
If possible, the application should avoid incorporating user-controllable data into redirection targets. In many cases, this behavior can be avoided in two ways: Remove the redirection function from the application, and replace links to it with direct links to the relevant target URLs. Maintain a server-side list of all URLs that are permitted for redirection. Instead of passing the target URL as a parameter to the redirector, pass an index into this list.
Vulnerable URL: https://www.tn.gov.in/contact
Payload:
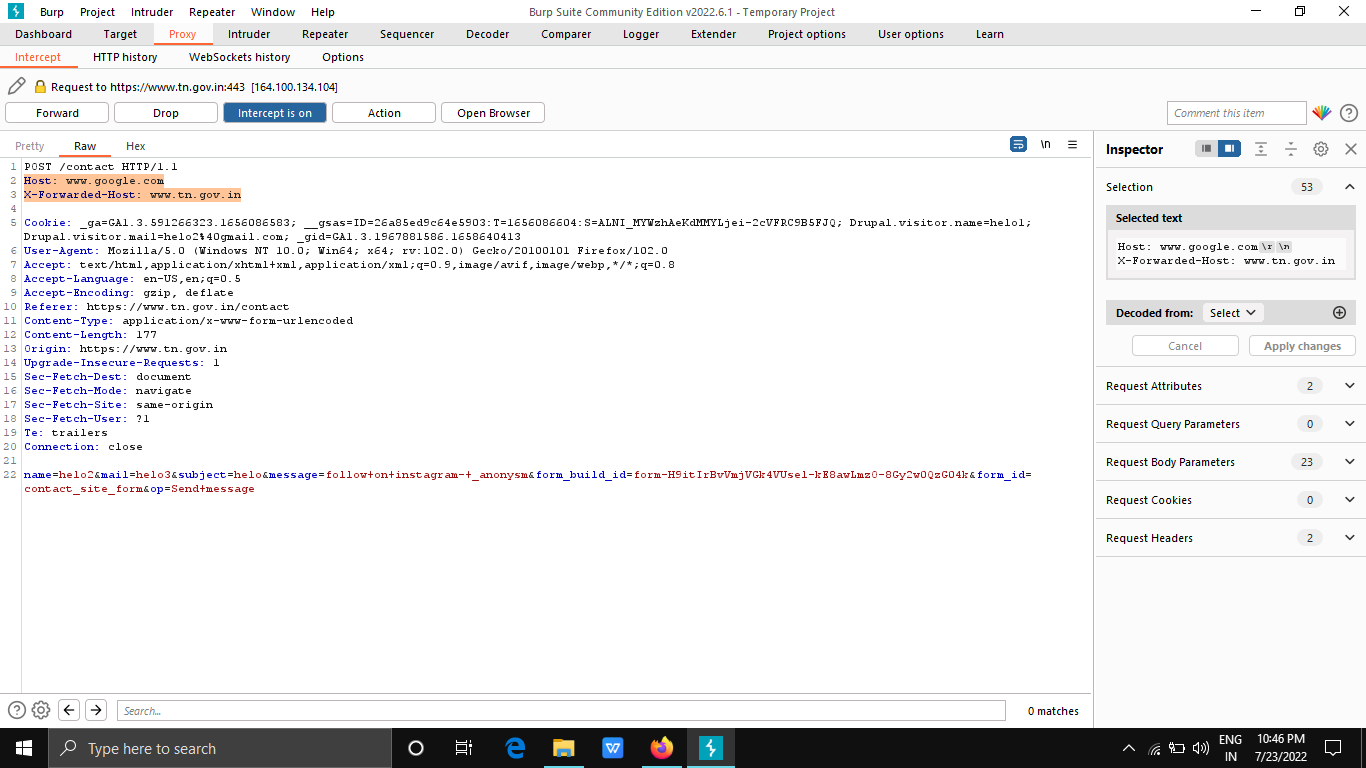
“Host: www.google.com
X-Forwarded-Host: www.tn.gov.in “
How to reproduce this vulnerability:
- Open this URL “https://www.tn.gov.in/contact “ and enter the name, email, subject, message and capture it intercept on Burpsuite.
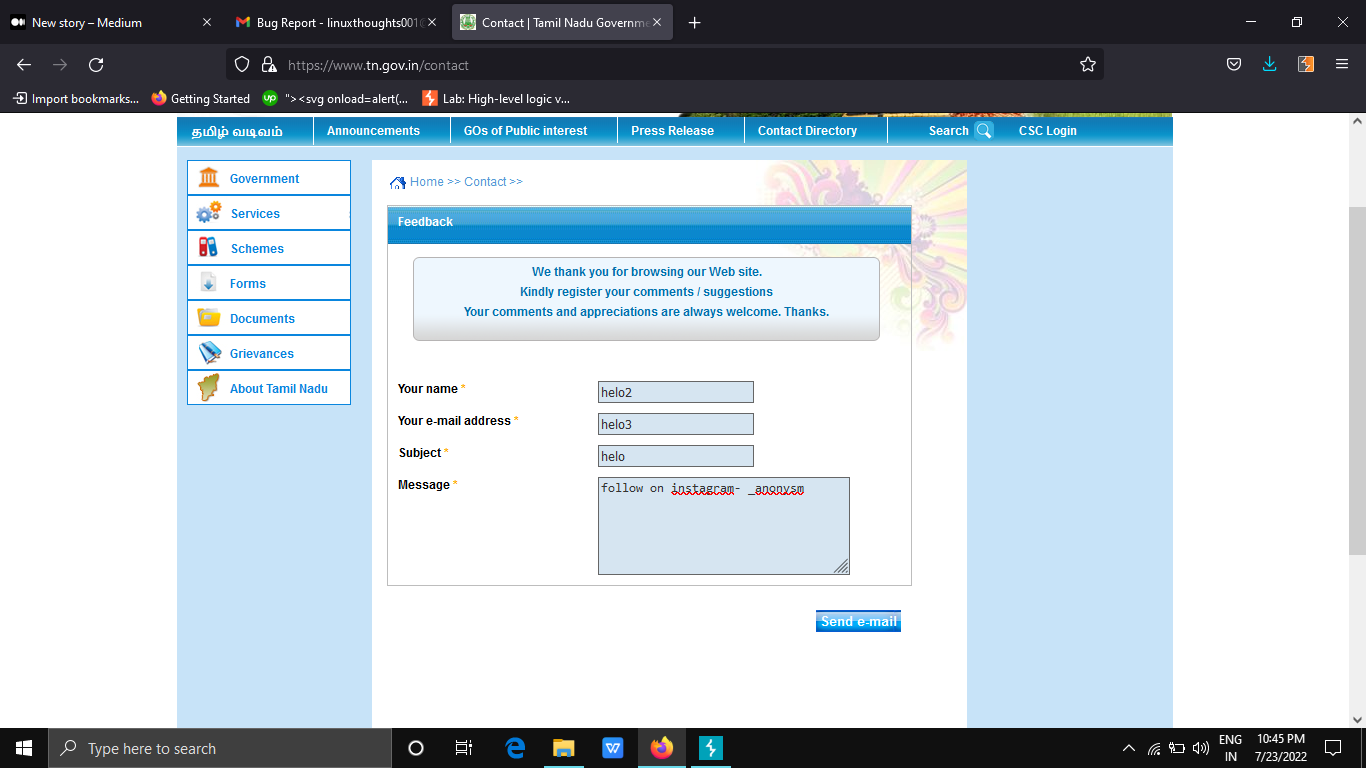
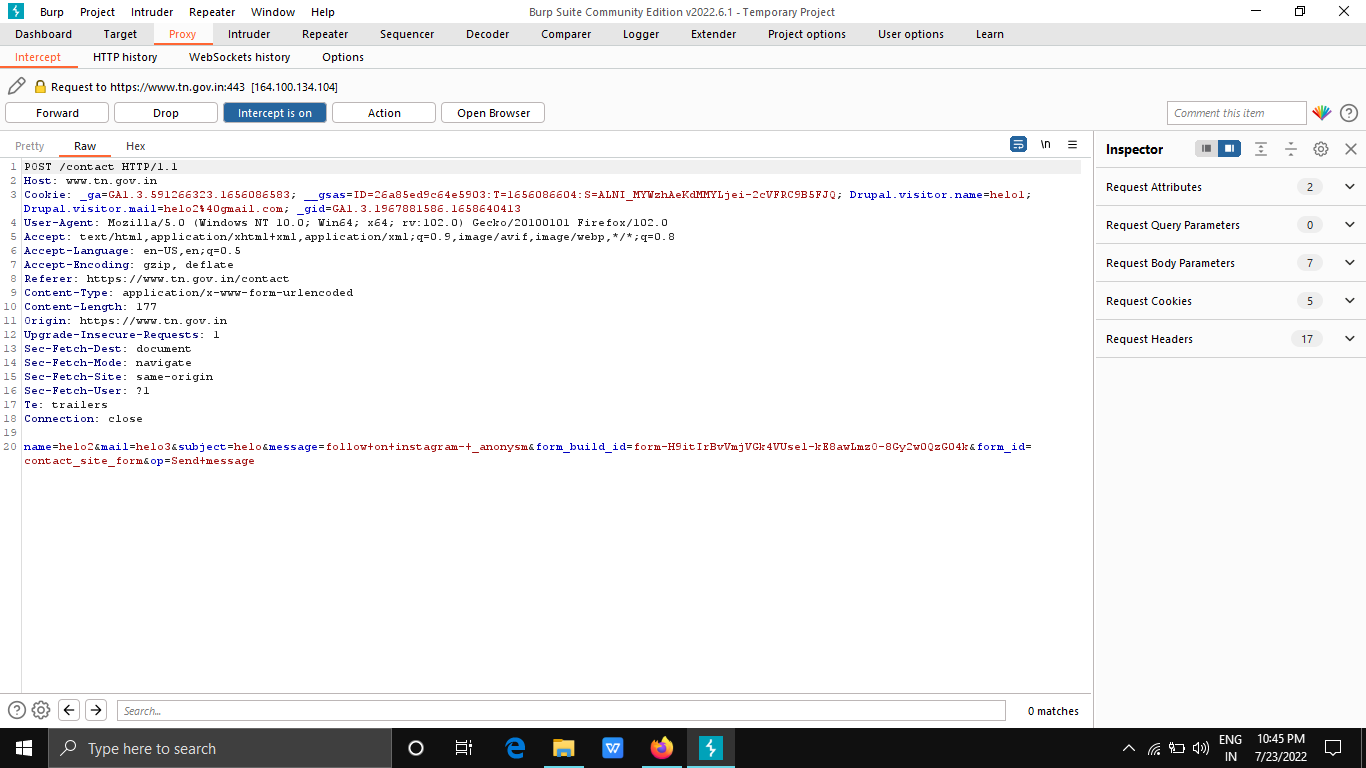
2.add the payload to the header request and forward the request.
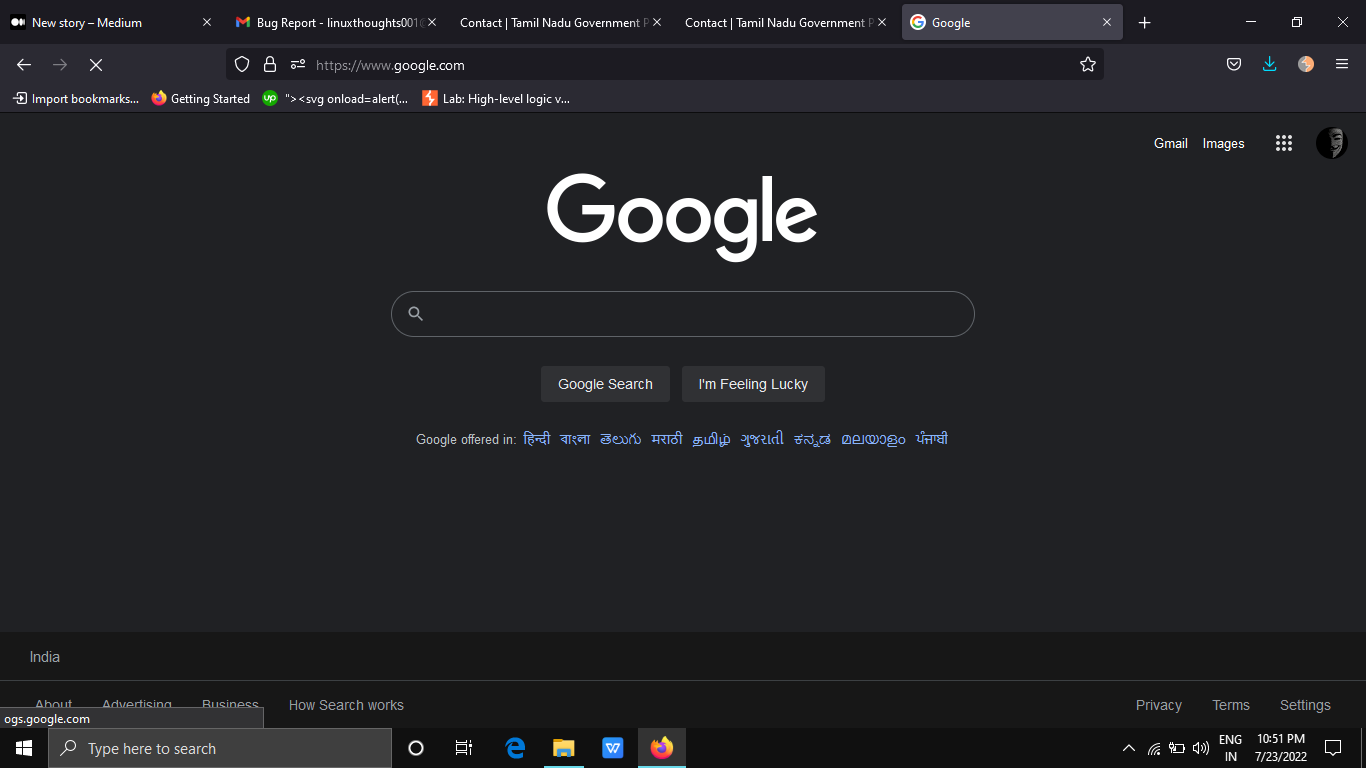
3.It will directly redirect to www.google.com.
If you are beginner try to find bugs in Government website to practice live website.
Finally bug found

You want full video of this bug follow on instagram
Impact
Impact: Whenever a user visits this URL, it will redirect them to site.com. It is used in phishing attack.

Post a Comment